18 January 2022
NIST Ransomware Profile. Why do we need it?
Ransomware! The biggest and scariest attack for every organisation. They are on the rise and continue to be a disruptive factor in the industry. NIST has come up with a recently issued a Ransomware Profile, currently designated as "NISTIR 8374". Organisations can use this guide to prevent, respond and recover from ransomware events. The Ransomware Profile was released on September 8, 2021, and is currently in a draft stage. The profile identifies security objectives from the NIST Cybersecurity Framework and aims to help organisations identify and prioritise opportunities for improving their security and resilience against ransomware attacks.
What is the Purpose of the Ransomware Profile?
NIST 800.53 is a huge 400-page document of security controls. To make this huge document more easier to understand for the private sector, NIST reorganised and condensed the most important controls and concepts into five functional categories: Identify, Protect, Detect, Respond, and Recover.
The Ransomware Profile aims to simplify the Cybersecurity Framework further. It breaks down the controls and offers practical steps that organisations can take to safeguard their networks from potential ransomware attacks. Organisations can utilise the report to manage the risk of ransomware and gauge their level of readiness in mitigating and responding to ransomware attacks.
Benefits of the NIST Ransomware Profile:
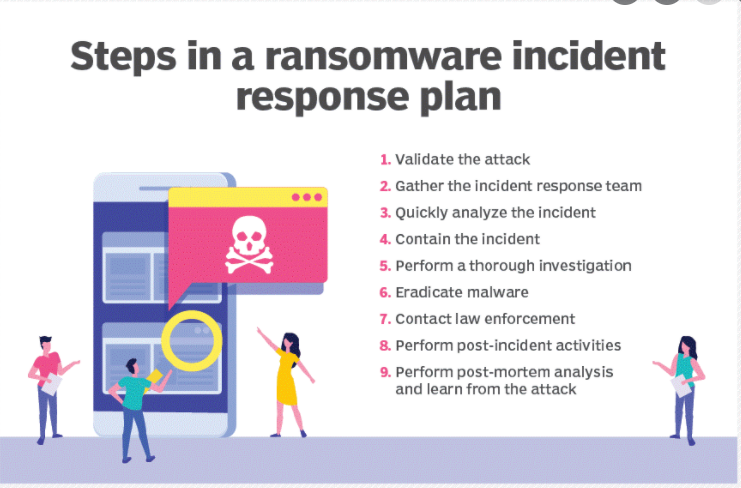
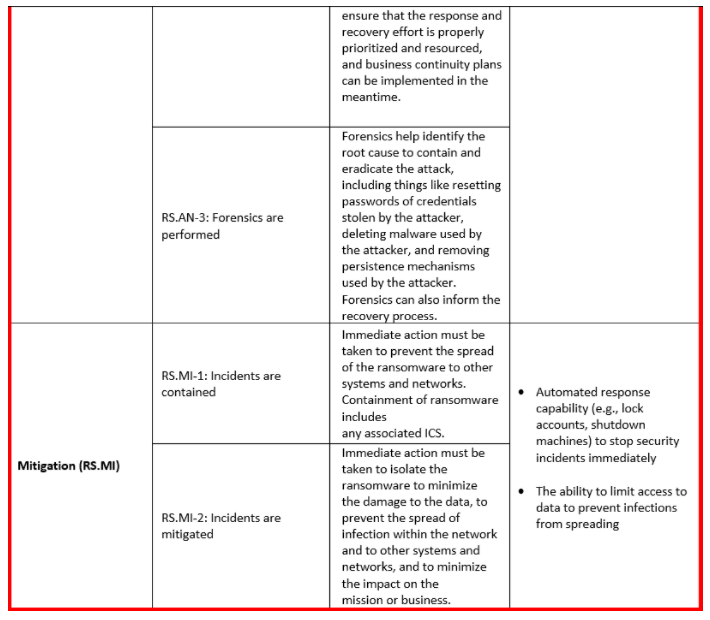
The NIST Ransomware profile aims to cover a good set of basics of ransomware resilience plan. If these policies are established in your organisation, you should be in good shape.
Identifying risks - The need for defining your digital assets and knowing what's important. This is the first step to data-first security and will help you understand where your critical data lives, and help you protect this sensitive data from breaches.
Place security your controls - Next, you should map your folders and permissions and implement a Zero Trust, least privilege model for your data. NIST requires that you manage who can access your critical data, and make sure you can report on who can and does access this data. An attacker's job is much easier if they only need to compromise one account to get access to your sensitive data. Do everything you can to limit access to important and sensitive data so that employees can only access what they need to do their jobs and you will significantly reduce the blast radius of an attack.
Continually monitoring for threats - Once you've locked down critical data, monitor and profile usage so you can alert on abnormal activity and investigate quickly. Attackers are more likely to trigger alarms if they have to jump through more hoops to access sensitive data.
Implementing a response and recovery program - NIST requires you to have measures to respond to and recover from security incidents. If you understand where your sensitive data lives, who has access to it, and how they're using that data, it will be much easier to investigate and even stop an incident in its tracks.
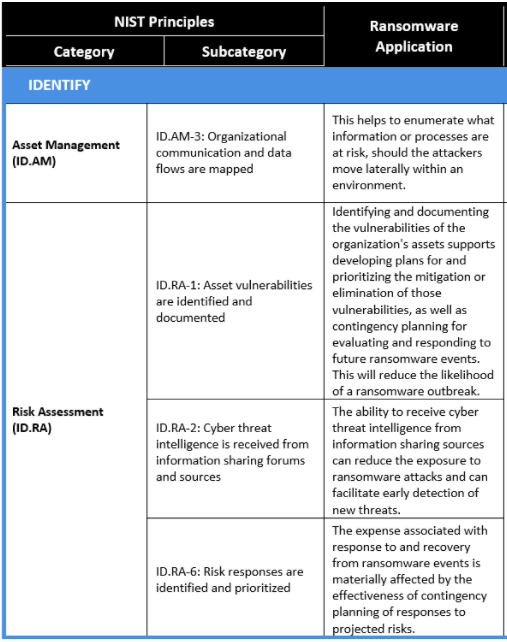

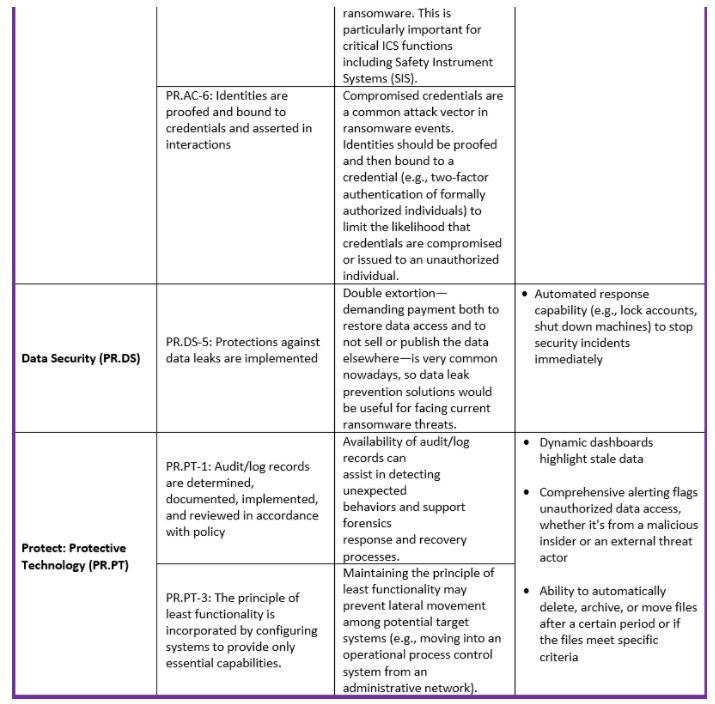
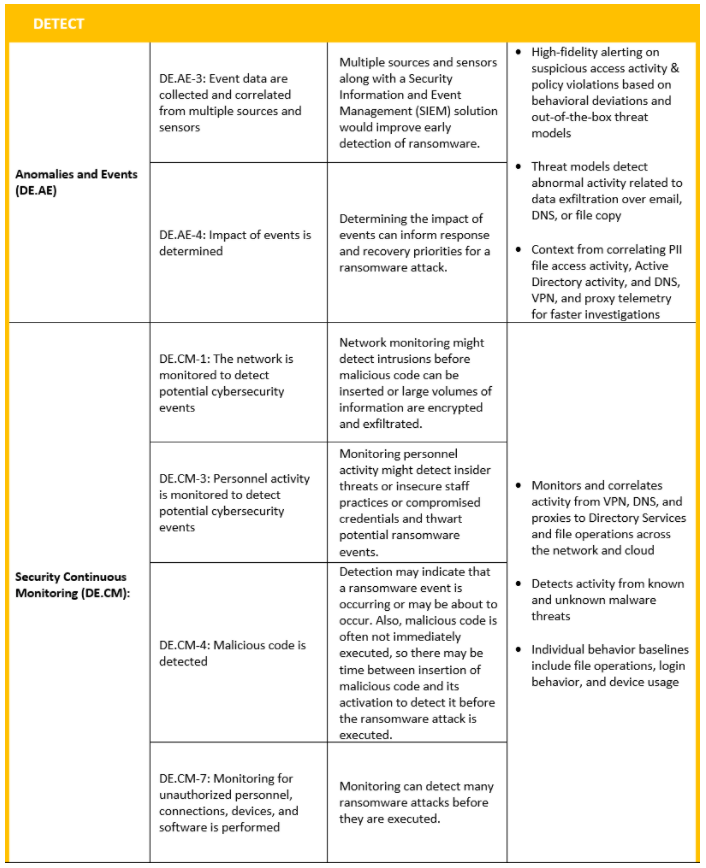

The NIST Ransomware Profile is still in draft stage, lets see what changes and new implementations NIST is planning for the upcoming revisions.
